Date: May 11, 2023
Summary: On April 28, 2023, a DeFi exploit was executed against the 0VIX Protocol. The attack involved flash loans, price manipulation, and a toxic liquidation spiral that led to the attacker’s profit. The full attack was executed in one single transaction at Polygon PoS blockheight #42054769.
I. Attack Overview
On April 28, 2023, at 10:45:16 AM +UTC, an attacker targeted the 0VIX Protocol at block height 42054769. The attacker used three addresses (0x407, 0x49c, 0x702) to execute a sophisticated exploit that involved flash loans, price manipulation, and a self-executed toxic liquidation spiral. All of this occurred within one transaction composed of 278 events. The attack resulted in a net liquidity loss of $4.33 million for the 0VIX Protocol with funds being sent to multiple different smart contracts before bridging 1069 ETH via Stargate Finance to Ethereum and subsequently depositing to tornado cash. The net flow of funds across all entities involved in the exploit is shown in the summary chart below.

Summarized net flow of funds across all entities involved in the attack. Unmanipulated (pre-exploit) GHST and vGHST prices were used to compute $-denominated values. Total accumulated AMM fees were derived to match final balances on all entities. Flow amounts within 0VIX should be read as indicative due to the changing oToken share price throughout the attack. Final balances can nonetheless be considered accurate to 0.1% precision.
II. Attack Flow
A) Setup
The attacker initiated the exploit by using address 0x407 to flashloan a total of 24.5M USDC, 6.15M USDT, and 1.95M GHST from the AAVE and Balancer platforms. The 6.15M USDT was deposited into the 0VIX Protocol and used to borrow various assets, maxing out the 0x407’s borrowing limit. The attacker’s borrowing ignored the stMATIC, jEUR, gDAI, and MAI markets.
Subsequently, 0x407 transferred 24.5M USDC and 283.146k vGHST (minted with a portion of the flash loaned GHST balance) to 0x49c. The latter deposited the funds into 0VIX Protocol and borrowed more stablecoin liquidity, looping all available vGHST in the process (totaling 11.392M vGHST in borrows). 0x49c also borrowed 720k USDC and 5.419M USDT. The borrowed funds were then transferred back to 0x407 along with the entire ovGHST balance accrued during the looping process. At the end of these operations, 0x49c’s portfolio remained overcollateralized with a loan-to-value ratio (LTV) of 79.7%.
B) Exploit
Next, 0x407 manipulated the vGHST price using the 1.656M GHST remaining from the initial flash loan to inflate the vGHST-GHST exchange rate from 1.03 to 1.78. The oracle used by 0VIX, that was built according to GotchiVault’s recommendation, computes the exchange rate as the ratio between the total amount of GHST tokens in the GotchiVault relative to the vault’s outstanding shares. By donating the GHST to the vault via GHST.transfer(vault) instead of vault.enter(), the attacker modified the total GHST held by the vault without changing the amount of shares. This caused a 72% spike in the ovGHST price. As a result, 0x49c’s vGHST borrows increased in value, making the portfolio undercollateralized with a LTV of 135%.

Loan-to-Value (LTV) evolution of 0x49c’s portfolio over the course of the exploit. X-axis tracks the number of events involving 0x49c’s funds.
The attacker used 0x407 to trigger 24 consecutive liquidations, repossessing USDC from 0x49c. Due to 0x49c having a LTV greater than the toxic threshold of 90.9% (liquidation incentives on 0VIX are statically set to 10%), each liquidation increased 0x49c’s LTV instead of reducing it. This guaranteed that liquidations would continuously be executable, known as a toxic liquidation spiral. The spiral ended when all of 0x49c’s collateral was repossessed, leaving a total bad debt of $6.46 million on 0x49c’s portfolio. A portion of the bad debt created, worth $735k, was captured as a fee share for the protocol. Due to the leveraged nature of the protocol, the attacker accounted for the liquidation fee (that 0VIX would have gotten) by borrowing sufficient USDC amounts such that, by the end of the attack, the available USDC liquidity had been completely drained.
C) Exit
After the liquidation spiral terminated, 0x407 redeemed 23.765 million USDC and 336k vGHST from the protocol. From starting flashloans worth $32.8M, of which $30.92M were directly deposited to 0VIX, 0x407 withdrew a gross amount of $35.19M in token value from the protocol. It includes recuperated flashloaned funds, the $6.46M of bad debt left on 0x49c, 0x407’s overcollateralized leftover position nominally worth $1.39 million, and the liquidation revenue share of $735k nominally paid to 0VIX.
The total extracted value post-exploit amounts to a net total of $4.33 million, paid out of 0VIX’s user funds. Of these, 1.4M GHST excess tokens remained with the GotchiVault where they were used to process further withdrawals by users selling into the price increase until the vault was finally halted and 978K GHST tokens are in the process of being returned to 0VIX by the Aavegotchi DAO and GotchiVault DAO. The attacker proceeded to swap all assets to repay the initial flash loans and convert remaining funds to ETH. Due to the sudden increase in GHST price, many of the swaps incurred significant slippage costs. Overall, 0x407 incurred $792k in total costs. Whether the attacker had other liquidity deployed into AMMs to attempt capturing any portion of these slippage costs is still unknown.
The remaining ETH was then bridged to Ethereum via Stargate and deposited into address 0x702. The attacker immediately deposited 520 ETH into Tornado Cash, transferring another 239 ETH on the following day. After keeping the remaining 310 ETH silent for over a week, 0x702 sent the last batch to Tornado Cash on May 9th. As of writing, 0x702 does not hold funds any longer.
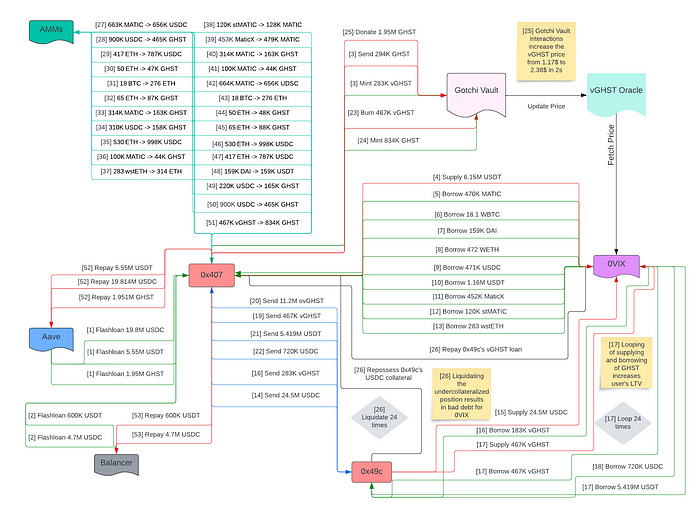
Detailed technical flowchart of the exploit tracking underlying token funds flowing across all entities involved in the attack.
III. Aftermath
The attack was spotted in real-time by our security partners at Hexagate. All protocol contracts were quickly halted. Prior to halting, an extra $280k worth of liquidity exited the protocol through normal operations. Security partners immediately followed the attacker’s funds onto Ethereum and were the first to point out 0x407’s major GotchiVault interaction. The 0VIX team quickly contacted the GotchiVault team who halted their contracts 12 hours after the exploit. During that time a number of users managed to sell their vGHST tokens into the price spike. Investigations have identified one particular user (0x797ef3a808092557c6c54a0fae161fb41a3ccc5e) who managed to extract 255,786GHST tokens (Worth $256,000 at the time of writing) in net profits as a result of the price manipulation about 2 hours after the attack.
Following a GotchiVault DAO vote which resulted in an unconventional solution on how to distribute stolen funds, 0VIX has recovered an initial sum of 206k vGHST. The remaining 763k GHST used to enable the exploit is currently still held by the AaveGotchi DAO, and all affected parties continue to work towards an agreement as AaveGotchi DAO has been reticent on whether to return the funds or not.
Whereas the funds used to trigger the price manipulation came directly from an AAVE flashloan, the same flashloan was repaid with 0VIX user funds. As such, the remaining GHST amount cannot be decoupled from the exploit as a whole.
At time of writing, the currently available liquidity on the protocol is as follows :

IV. Conclusion and Discussion
The 0VIX Protocol suffered a significant loss due to a well-coordinated atomic DeFi exploit that leveraged flash loans, price manipulation, and a self-inflicted toxic liquidation spiral. In the exploit’s immediate aftermath, 0VIX Protocol’s net TVL (total supplies minus borrows) sat at $1.4 million worth of value, compared to a pre-exploit amount of $5.8 million. After accounting for the subsequent $280k of asset withdrawals prior to the full halting of contracts, the total liquidity currently held by the protocol sits at roughly $1.2M (see table above). This number does not account for the additional $960k expected from GotchiVault/Aavegotchi recuperation process.
This incident highlights the risks of a toxic liquidation spiral once triggered. We take the opportunity to reiterate that this vulnerability is currently present in all DeFi protocols whose core codebase is based on Compound and AAVE forks, thus deserving urgent attention. Oracle prices can be manipulated in a multitude of ways, toxic liquidation spirals, on the other hand, always follow the same fundamental mechanic.
To prevent this now known common risk the team has already started working on remedying it. Liquidation incentives need to either scale with a liquidated user’s loan-to-value ratio or liquidations be halted altogether whenever a user’s loan-to-value crosses their toxic liquidation threshold. Implementing these changes on 0VIX requires significant changes to the core contracts. This involves considerable developer time, risk assessment and arranging new audits. Although the 0VIX core team was in the process of actively working through these, the exploit occurred before security changes and enhanced risk measures could be fully implemented.
Looking at the wallet activity and contract deployments it is evident that tests and preparations were made prior to the execution of this attack. Moreover, we found that the attacker deployed a few similar contracts around an hour before the attack from different wallets (0xbef, 0xb3d). The actual exploiting contract was deployed a minute before the attack. After decompiling all suspicious contracts, it was found that many couldn’t work because of faulty accounting of fund flows. More specifically, the older contracts attempted to perform 25 liquidations instead of 24. The attacker ultimately deployed the final version of their contract one minute before the attack and exploited the protocol in one transaction.
V. Acknowledgements
Special thanks to 0VIX’s main security partner Hexagate, who have been instrumental in spotting the attack in real-time and helping with the analysis of the attack, fund flow, and damage assessment. Post-attack we intend to intensify our relationship even further and will be announcing more on this in the near future, as Hexagate were able to detect the malicious contracts upfront.
Steps to Recovery
The 0VIX Protocol Association is pursuing its investigation with the help of law enforcement and security experts on tracking the attacker and bringing them to justice. Everyone is fully dedicated to recoup as much of the stolen liquidity as quickly as possible and distribute this to all affected users.
It is in everyone’s interest to make everyone whole, both the community and the protocol.
From the net liquidity loss of $4.33 million, 978.3K GHST are due to be swapped and transferred to 0VIX at a current value of $0.96m, resulting in a liquidity gap of about $3.3m (at the time of writing).
As it currently stands, the total available liquidity on 0VIX is approx. $2.3m (incl. the GotchiVault/Aavegotchi funds).
Even though a portion of bad debt ($735k) was captured as a protocol fee, this fee cannot be withdrawn and distributed to affected users as there is no sufficient USDC liquidity. Therefore, it may be suggested to burn these fees and decrease the bad debt by $735k.
The Association will appeal to the Aavegotchi DAO to return the stolen 768k GHST (currently worth around $752k) in their possession to 0VIX users. It seems that the Aavegotchi DAO would like to understand the situation in greater depth before proceeding with any actions regarding the 768k of GHST exploited from 0VIX users that Gotchivault sent to the Aavegotchi DAO treasury. The first step here is publishing this post-mortem and helping to answer any questions from Aavegotchi DAO members.
The Association will propose options to the community in a governance proposal for how to distribute funds to affected users as soon as any funds were to be recovered. There are a few options to consider and these options are now being diligently researched to also understand potential repercussions and will be shared with the broader community in due course.
Once there is a recovery plan in place and safety checks and additional upgrades have been implemented, operations on 0VIX PoS will resume.
The following security upgrades are currently put in place prior to resuming 0VIX Polygon PoS:
1. In the first stage, full integration with security partners that detect malicious on-chain activities and pauses protocol operations before an exploit or hack can be executed.
2. As soon as viable, implementation of a mechanism to pause liquidations in the event of a toxic liquidation spiral, therefore, considerably safeguarding the protocol from insolvency risks.
Stay up to date by following the official Twitter. For any questions and to join the hub of our community go to 0VIX’s Discord.
Twitter | Discord | Telegram | Website | Hexagate
Disclaimer
Not financial or tax advice. This blog is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. This blog is not tax advice. DeFi and the overall Crypto space are still developing and there are risks involved in engaging with them. Talk to your accountant. Do your own research.
